The world will overcome the Coronavirus pandemic, but are organizations ready for the day after?
By Yael Macias, Product Marketing Manager, Endpoint and Mobile Security
As the world slowly approaches a new dawn, reaching the light at the end of the very dark tunnel that has been the Coronavirus pandemic, its effects on every aspect of life have left a trace that most likely will remain for years.
The rapid spread of the virus has dramatically shifted the way organizations work. True, digital transformation and remote accessibility have been increasingly adopted in the past decade, and yet barely –though understandably– any organization was prepared to go fully remote from one day to another. The new reality, exponentially accelerated by the pandemic, is the perimeter-less organization. While most organizations had an infrastructure and policies that allowed having remote access to some corporate resources, almost no organization had the measures in place to allow full, secure remote access of their entire workforce in order to do their job, or at least most of it.
The reality is quite different when it comes to malicious actors seeking new ways to attack organizations. Malicious actors are dynamic, move fast, and look for any security hole left when organizations adopt a new IT infrastructure. To no one’s surprise, there are many. In fact, attack surfaces are exploding and remote endpoints, such as laptops and mobile devices, are a very attractive backdoor to ultimately breach an organization’s entire network.
Leveraging the state of uncertainty and fear, hackers have succeeded to compromise endpoints and the data they contain by systematically tricking users. A few weeks ago, Check Point researchers uncovered 16 apps masquerading as Coronavirus apps. Users would visit what they thought was an informational site, and unsuspectedly downloaded malicious apps to their devices that could expose their sensitive data. And this is just one example. In mid-April, Google reported that in just one week, it saw more than 18 million daily malware and phishing emails related to COVID-19 scams sent via Gmail alone.
One may argue that once the pandemic is over, people will go back to working as they were before. That corporate information will go back into the safe perimeter, closing a dark chapter of any IT department. But this assumption is probably very far from the reality. A cyber pandemic is most likely around the corner, and the Coronavirus has only accelerated a trend that was already in motion: an enhanced flexibility when it comes to the workplace. And that, is here to stay.
The good news is that a digital transformation does not need to come at the expense of security. IT admins usually face the dilemma of productivity vs. security, and at a time when organizations need to reassemble their entire workflows, many organizations are adopting the “looking to the other side and hoping for the best” approach. However, innovating in a fast-paced world doesn’t need to come at the expense of security. Unlike with the Coronavirus, prevention in IT security does exist and the cyber pandemic is coming with previous notice.
To address the massive reshaping of the modern workforce in the post-Coronavirus era, Endpoint Protection solutions play the critical role in protecting against today’s threats.
So how can organizations enable a productive remote workforce without compromising on security?
Prevention-first approach
It is much less costly and time-consuming to prevent an attack, than to detect and remediate it after it has breached the network and caused damage. That is why it is key to invest in security technologies that leverage Artificial Intelligence, behavioral threat assessments, and real-time Threat Intelligence, and do not rely on signatures only.
 Figure 1 SandBlast Agent uses CPU-level emulation to prevent exploits and delivers sanitized versions of documents within seconds
Figure 1 SandBlast Agent uses CPU-level emulation to prevent exploits and delivers sanitized versions of documents within seconds

Figure 2 SandBlast Mobile’s cloud-based Behavioral Risk Engine runs downloaded apps to assess their risk level. It also leverages ThreatCloud’s real-time threat intelligence
Automated remediation features and contextualized insights
Invest in endpoint security solutions that have the ability to quickly triage events, contain infections, fully sterilize the systems, and provide IT admins with full visibility and insights into the attack. This will allow for the peace of mind that even if malicious actors manage to breach the defense mechanisms in place, no data will be compromised and the organization won’t suffer from downtime.
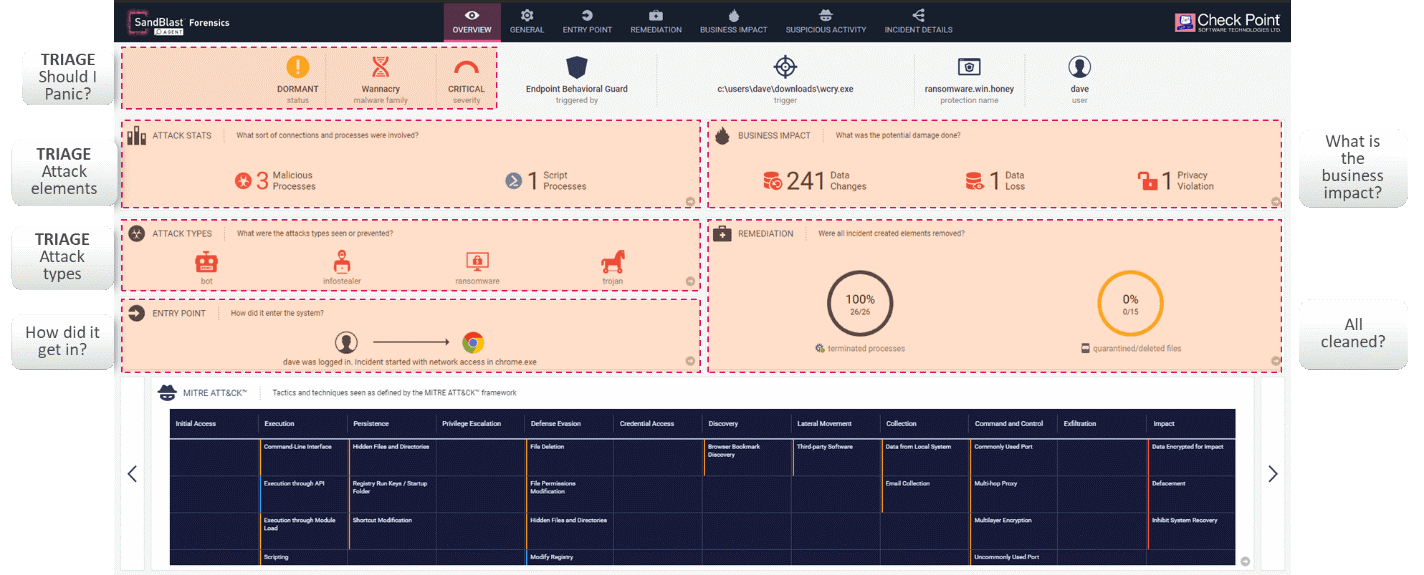
Figure 3 SandBlast Agent’s automated forensics report

Figure 4 SandBlast Mobile blocks access to corporate resources when the mobile device is at risk. It does so independently from UEM solutions
A cloud-based management console and scalable solutions that are easy to deploy
A remote, expandable, fully redundant and easy-to-use management is important now more than ever. A unified cloud-based management solution that delivers these capabilities and enables provisioning and monitoring of devices and policies from the cloud will make the ultimate difference when deploying endpoint security solutions.
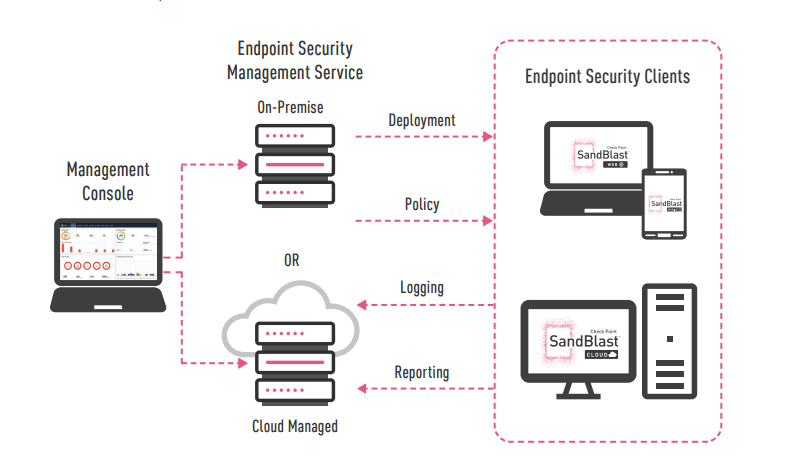
Figure 5 SandBlast Agent and SandBlast Mobile can be easily managed through the cloud-based Infinity Portal
The Pandemic will disappear. Its Cyber Effect is here to stay.


